Security has been one of the fastest-growing concerns for CIOs in the past years. For good reason, every day, we see more headlines about the latest big breach – Solar Winds, Colonial Pipeline, Uber. Leaders are looking for new ways to secure their important assets to combat the growing threats facing businesses. Concepts of Multi-Factor Authentication (MFA), Zero Trust Architecture and DevSecOps are a few recent trends. These trends were starting to gain traction before the COVID-19 pandemic. Even former President Obama addressed it in 2016, and adoption has accelerated with the rise of remote work triggered by the pandemic. Hybrid work seems to be here to stay, and the one constant in cybersecurity is more change.
While the networks under protection are subject to constant change, the tools used to secure them continue to be based on a set of design principles established decades ago. The concept of Design Principles has been around for ages and in many different forms. The Interactive Design Foundation defines design principles as “guidelines, biases, and design considerations that designers apply with discretion” and “fundamental pieces of advice for you to make easy-to-use, pleasurable designs.” Design principles have been used in technology, most commonly in User-Interface design, but they can also be used in application design and in designing security controls.
Taking a deeper look at MFA and Zero Trust
As the networks and systems under protection change and evolve, the tools used to secure them do as well. Two concepts have recently been introduced to help ensure better protection from all threats, internal and external. Many are likely familiar with MFA and use it in their daily lives. MFA is the concept of needing two or more separate attributes to authenticate to a system. Each of these attributes typically falls into one of three buckets: something you know, something you are, and something you have. MFA requires the user to prove their identity using at least two of these buckets.
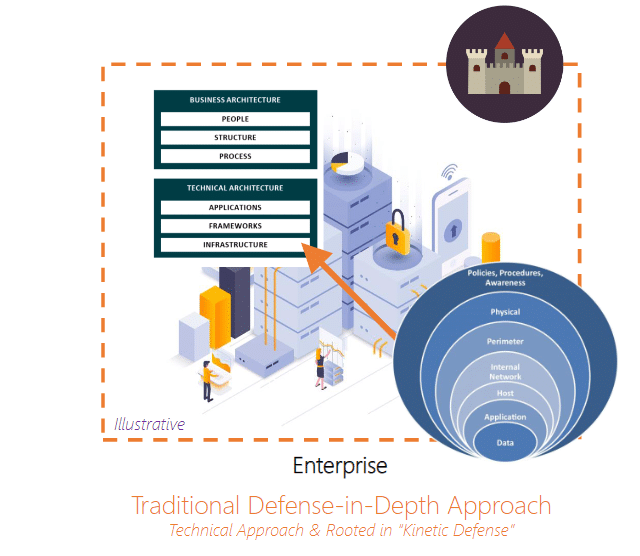
On the other hand, Zero Trust architecture may be a new concept for many, especially those not in security. According to Microsoft, the key Zero Trust principles are to verify explicitly, use least privileged access and Assume breach. Microsoft also provides the following definition “Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network…”. What does this mean? Zero Trust ensures every request to a resource has verification that the requestor is authorized. Said another way, just because you are inside the castle walls does not mean you are friendly.
The adoption of MFA and Zero Trust is growing. Many users have become familiar with MFA using it often, if not daily. Zero Trust is more transparent to end users, and likely a new concept to many. Why are these two trends growing? It ultimately boils down to better organizational and personal security, but there are different driving factors for each trend. A common understanding of Moore’s law highlights that computing performance doubles every two years. That is a lot of increased performance since the first computer in the 1940s. As computing performance increases, the speed and ease to crack passwords decrease. This inverse relationship creates an environment where using a single password to protect sensitive data is no longer secure.
Additionally, as more research is put into quantum computing, the potential for modern encryption to be broken continues to rise. This is where MFA comes into the picture. Access is no longer a competition between the resources to crack the password and the strength of a single password hash. There are now multiple factors that need to be compromised to access sensitive data.
The driving factor behind MFA is computing performance. For Zero Trust, it is about computer (hardware) location. As organizations adapt to a world of cloud computing and remote work, the critical infrastructure that companies rely on is no longer only in an on-premises data center behind locked doors or entirely on a corporate network. The rise of cloud computing pre-pandemic provided the ignition, but the rise of remote work was the real flash point for Zero Trust Architecture. Companies now need to provide access to internal resources outside of their physical building where network access can be closely controlled and monitored. As employees log in from the comfort of their homes and applications run on cloud infrastructure, companies need to ensure that access to internal resources is authorized for every request. Networks today look more like Figure 2 than Figure 1, and because of this, Zero Trust is on the rise.
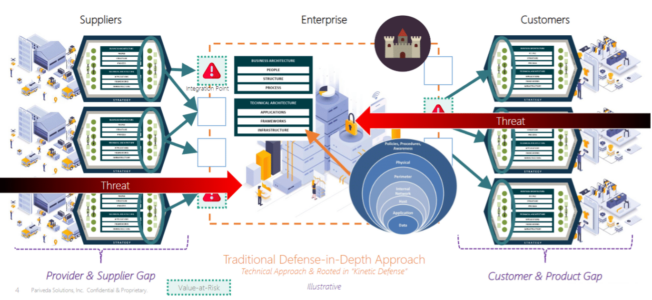
MFA and Zero Trust are advocated for as new security approaches for a new security environment. While the security environment we face today has definitively evolved, are MFA and Zero Trust new concepts? Are new security concepts needed to effectively protect ourselves in the complex environment we find ourselves in?
Security design principles
In 1975 Jerome Saltzer and Michael Schroeder wrote a paper for Institute of Electrical and Electronics Engineers (IEEE). The paper was entitled The Protection of Information in Computer Systems. This paper, written based on the author’s experience, listed eight security design principles that are important in designing secure software systems. These eight security design principles are[1] :
- Economy of Mechanism: Keep the Design as simple and small as possible
- Fail-Safe Defaults: Base Access decisions on permission rather than exclusion
- Complete Mediation: Every Access to every object must be checked for authority
- Open Design: The design should not be secret
- Separation of Privilege: A protection mechanism that requires two keys to unlock is more robust and flexible than one that allows access to only a single key
- Least Privilege: Every program and every user of the system should operate using the least set of privileges necessary to complete the job
- Least Common Mechanism: Minimize the number of mechanisms common to more than one user and depended on by all users
- Psychological Acceptability: Human interface must be designed for ease of use so that users routinely and automatically apply the protection correctly
This is only a brief description of each principle; I invite you to read the Design Principles section of the paper if you are interested in more detail of each. As we look at what each of these principles represents, there are clear similarities between them and current “new” security concepts, and least privilege is probably the most well-known security concept.
- Complete Mediation: Check every access to every object for authority
- Zero Trust: Verify each request as though it originates from an open network
Comparing Complete Mediation and Zero Trust, it is clear that Zero Trust is no more than an application of Complete Mediation. Zero Trust applies the concept in the context of network access as that is the environment in which we must currently operate. The concept though is the same – check/verify every request to access every object to ensure that it has the authority/permission to have access. One of the newest security concepts is simply a modern application of a decades-old security principle.
- Separation of Privilege: “In a computer system, separated keys apply to any situation in which two or more conditions must be met before access should be permitted.” (Saltzer)
- Multi-Factor Authentication: needing two or more separate attributes to authenticate to a system
The above two concepts are practically identical. Separation of privilege requires two or more conditions to be met. This might as well be the definition of Multi-Factor authentication. Another “new” security trend is not all that new. In fact, this one can be taken even further back than Saltzer & Schroeder. Think about access to a safety deposit box at the bank. You have a key (something you have) and must provide identification to the bank for them to use their key with yours (something you are).
Are there actually any new security concepts?
Over the years, there have been attempts to compile new security principles and concepts. The Cybersecurity and Infrastructure Security Agency (CISA), established in 2018, has put out a white paper on Principles and approaches for Security-by-Design and Security-by-Default. This work touches on many of the same concepts referenced in the 1975 IEEE paper as well as adding a few code-specific actions, such as static and dynamic application security testing. In 2012, IEEE, where the original paper was published, published a paper entitled A Contemporary Look at Saltzer and Schroeder’s 1975 Design Principles. This paper looks at the original 1975 principles and books and papers written since and lists its own eight security principles. While many are the same, there are two notable additions:
- Continuous Improvement: Continuously assess and make changes to improve results
- Chain of Control: Ensure that trustworthy software is being executed – similar to the chain of custody concept for physical evidence
This 2012 paper introduces only a few additions, mostly operating principles, to the original principles.
Cloud security design principles – AWS & Microsoft
There may be only a few journals written on Security Design principles in the last ten years. However, today is all about the cloud. The cloud is part of why Zero Trust is growing or Complete Mediation is making a comeback. The major cloud companies both have lists of design principles (AWS, Microsoft). These design principles contain some new items, primarily around data encryption and preparing for security events. However, an argument could be made that Fail-Safe Defaults cover a good portion of the “new” concepts listed.
Old is new again
Change is necessary and constant in a volatile, uncertain, complex, and ambiguous (VUCA) environment such as today. The location of workers, the tools being used, suppliers, data centers, and more are constantly adapting and changing. Security teams must adapt to this change with the rest of the organization. By leveraging design principles, both current and original, that ensure security, teams can continue applying new tools to meet their needs and adapt to constant change while continuing to protect from every threat.
Cyberattacks are grabbing more and more headlines in major news outlets. With every new headline, security becomes a bigger question for business leaders. Despite this, the core concepts of security haven’t changed all that much; a few new additions, but the key concepts still hold true. By leveraging these design principles that have stood the test of time as a framework for your organization, you will be able to respond to every new change and remain protected from the barrage of attacks that face every company.